
Written by Xavier Smith08/02/2024
Virtual private networks (VPNs) – Infrastructure Security – Keeping Your VPC secure
Virtual private networks (VPNs)
VPNs are essential for creating secure communication channels over the internet and connecting VPCs to on-premises networks or other external networks. There are two types of VPNs:
- Site-to-site VPN: This type of VPN provides a secure connection between an external network and a VPC using the internet protocol security (IPsec) protocol. It is facilitated through an encrypted tunnel between a virtual private gateway on the AWS side and a customer gateway on the external network’s side. Its primary application is to extend your network into AWS, effectively making AWS an extension of your data center or environments hosted with other cloud providers. For example, applications running in your VPC that require access to databases or resources in your on-premises data center can benefit from a site-to-site VPN. Moreover, for complex environments that require connectivity between multiple remote networks via VPN, AWS VPN CloudHub offers a more centralized solution. Acting like a transit gateway, it simplifies connectivity but is exclusive to VPN connections.
- Client VPN: AWS Client VPN is a managed service that offers secure and scalable remote access to resources within your VPC from any location using an OpenVPN-based client. This service is particularly beneficial for providing developers secure access to resources in private subnets, mitigating the need to expose these resources to the Internet. For example, if you need to perform SQL queries, a client VPN offers a far safer way to interact with your database compared to leaving it open to internet traffic.
Integrating key VPC components
The following diagram (Figure 2.1) presents a standard VPC structure featuring two private subnets across two AZs. It highlights how outbound traffic from these resources is channeled through NAT gateways (indicated by red arrows), while inbound traffic navigates from the internet to the resources via the ELB, as shown by blue arrows:
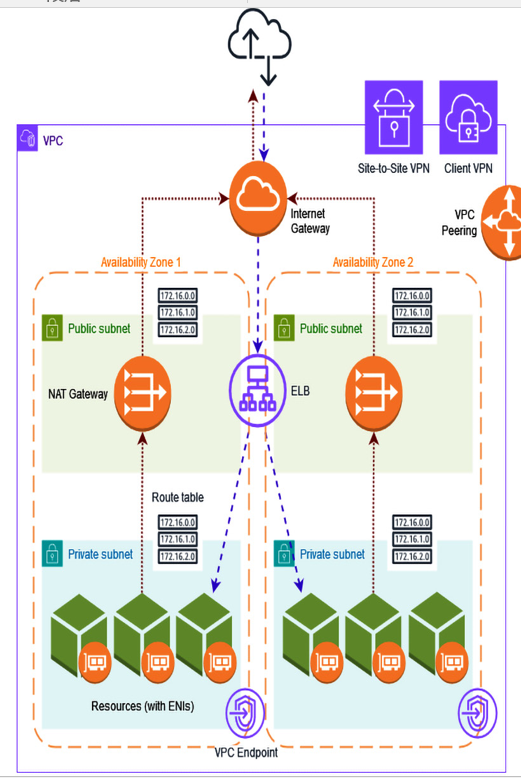
Figure 2.1 – VPC architecture
With the fundamentals in place, let’s focus on securing our VPC designs.
Archives
- August 2024
- July 2024
- June 2024
- May 2024
- April 2024
- March 2024
- February 2024
- January 2024
- December 2023
- October 2023
- September 2023
- August 2023
- July 2023
- May 2023
- March 2023
- January 2023
- December 2022
- November 2022
- August 2022
- June 2022
- April 2022
- March 2022
- January 2022
- December 2021
- October 2021
- August 2021
- June 2021
- April 2021
- March 2021
- January 2021

Leave a Reply