
Shared responsibility in practice – a closer look at AWS compute – Introduction to AWS Security Concepts and the Shared Responsibility Model
Shared responsibility in practice – a closer look at AWS compute
The shared responsibility model extends across AWS compute services, but the specific breakdown varies based on the level of abstraction. Here is how it applies to different options:
- Amazon EC2 (IaaS): AWS secures the underlying infrastructure – the hypervisor, physical hardware, and data center security. This grants you full control over the guest OS, applications, data, and network configuration. This flexibility comes with the onus of managing these layers for optimal security.
- AWS Fargate (PaaS): AWS extends its management to include the guest OS, patching and maintaining it for you. You focus on developing and deploying your containerized applications, along with data security and essential network configurations (such as security groups). This reduces operational overhead without sacrificing security control.
- AWS Lambda (PaaS): AWS takes on the responsibility for the infrastructure and the environment your functions run in. Your primary concern is ensuring your code is secure and that it manages any sensitive data appropriately. Additionally, if your Lambda function interacts with resources within a VPC, you may also need to configure network security elements (such as security groups).
The following figure (Figure 1.2) illustrates the division of responsibilities among those options:
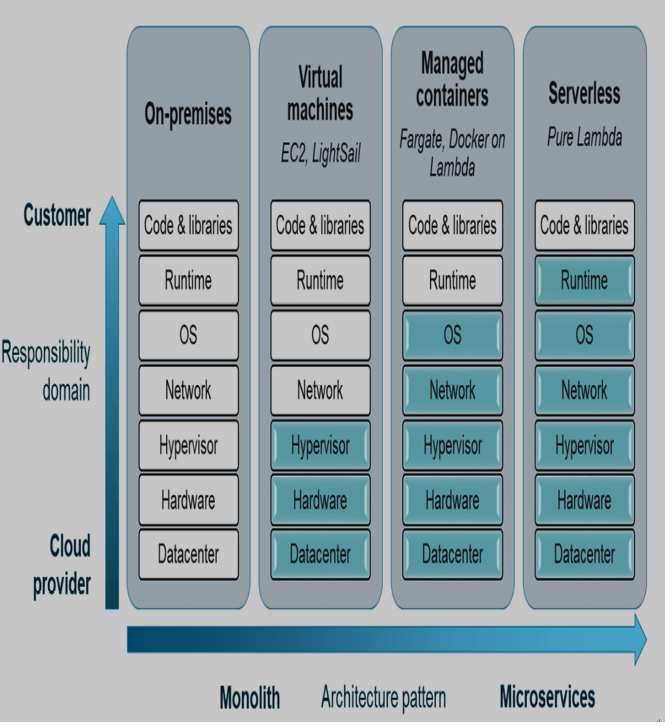
Figure 1.2 – Responsibility domain defined per compute type
It is worth noting that modern applications, especially those based on microservices architectures, frequently opt for managed cloud-native services (PaaS) such as Fargate or Lambda. These services provide more agility and ease of use, eliminating the need for customers to manage things the underlying operating system and networking. For example, a microservices-based eCommerce application could use Lambda for order processing, Fargate for inventory management, and S3 for storing product images, all without worrying about the underlying infrastructure. This means that the responsibility tends to shift more toward the CSP. This allows customers to focus more on their core business, leaving the heavy lifting of infrastructure management and security to AWS.
Archives
- August 2024
- July 2024
- June 2024
- May 2024
- April 2024
- March 2024
- February 2024
- January 2024
- December 2023
- October 2023
- September 2023
- August 2023
- July 2023
- May 2023
- March 2023
- January 2023
- December 2022
- November 2022
- August 2022
- June 2022
- April 2022
- March 2022
- January 2022
- December 2021
- October 2021
- August 2021
- June 2021
- April 2021
- March 2021
- January 2021

Leave a Reply